The internet is loaded with cyber threats more than you would ever have thought but unfortunately, most of us are not cognizant. Some assume that cyber criminals only focus on the high ranking politicians, celebrities and persons with high net worth. As it happened in 2014 when hackers gained access to White House systems and retrieved then-President Barack Obama’s sensitive communications. However, the fact is different! The cyber criminals and security hackers also target regular people like you and me, and they do this even more frequently.
Most Common Types of Cyber Security Attacks:
We have rounded up here the most common types of cyber security attacks out there.
Phishing:
Phishing is an attempt to obtain sensitive information such as username, password or credit card details. The hacker sends a bogus email with a link or attachment deceiving the receiver to click them. As the receiver clicks on the link or download attachment, it launches a malware in the system. Phishing attacks have been popular since the commencement of electronic mail and would remain same for the coming future.
Spear Phishing:
Spear Phishing is another version of a phishing attack targeting specifically to customers from a particular bank or user of an online shopping site. Since the users are used to receive emails for their relevant organization they won’t be as much doubtful and more likely to open that infected link or attachment.
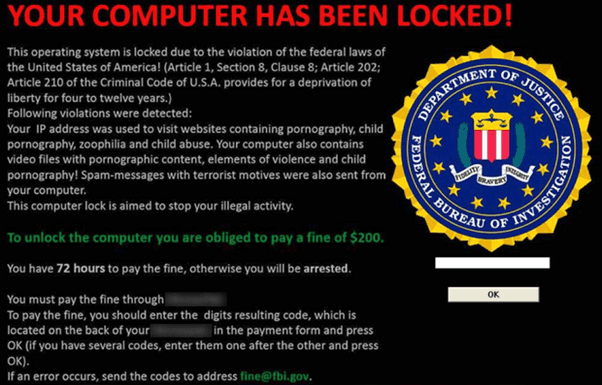
Ransomware:
Ransomware is the most advanced form of malicious attacks developing as the biggest cyber threat. It is a malware that is delivered to a device connected to the internet via a phishing email. As the receiver clicks on the infectious link or downloads and executes the attachment file, the ransomware begins its encryption attack. It threatens to publish victim’s data or restricts him from accessing its system unless a ransom is paid.
How to Improve Cyber Security:
Here are the ways to enhance cyber security and avoid the most common cyber security threats.
Password Protection:
Strong passwords are the first defense that can secure your system from data leaks, and changing them regularly can help keep the hackers away. Make regular password update compulsory and learn how to create and remember strong passwords.
Keep System and Software Updated:
The time you connect to the internet, the odds of exposing to the internet vulnerabilities escalate. To limit the possible threats, regularly implement system and software security updates. Whether using a personal computer or mobile phone, keep every application, operating system and internet connection up to date. The popular internet browsers keep releasing security patches in form of updates, so the moment you receive a message to update your browser, instantly download and install the available update.
Implement Virtual Private Network:
The networks that are protected only by simple security measures are more likely to be attacked by the malicious hackers. Implement virtual private network (VPN) for all connections within your workplace. Also, make it compulsory for your mobile workforce who may connect through public Wi-Fi services.
Eradicate Unused Services or Apps:
When you are using any trial version software or a program with limited duration, remove the program and associated login credentials immediately after it expires. In case you are not using any feature of a unified communications deployment, turn it off to limit unauthorized access.
Install Anti-Phishing Toolbar:
The popular internet browsers can be customized with anti-phishing tools to keep a check on the websites you visit and to notify you if you bump into a malicious site. As you launch a website, the toolbar compares it with the list of known phishing sites and alert you if there is any match. These toolbars cover you from phishing scams and are completely free.
Use Firewalls:
A high-quality firewall acts a shield between you, your computer and a malicious hacker. Use firewall both for your desktop and network as well. The desktop firewall is a type of software and the network firewall is a kind of hardware. When used together, they can drastically reduce the odds of phishers and hackers breaking into your system.
Use Antivirus Software:
Do not forget to install reliable anti-virus software on your device, and be sure to keep your antivirus software updated. While firewall blocks the cyber-attacks preventing access to malicious files, anti-spyware secures your device scanning every file which comes through the internet to your system.
Remember there is not a single way to avoid cyber-attacks, so stay vigilant and give a try to all measures to prevent invasion and have a trouble-free online experience.
Author Bio: Brooke is a tech geek and content manager at http://www.theonespy.com . She mostly writes about latest technology trends, software reviews, digital parenting, employee monitoring, relationships and all the work which needs research. Follow her on twitter @brookechloe78